
Please circulate this as widely as you can. I think it is even more massive than the issue of the DWP’s fake ‘psychometric test’.
There has been much attention in recent weeks on the Dept of Work and Pension’s (DWP) ‘cruel and unusual‘ treatment of jobseekers. It has forced claimants to take fake online tests under threat of losing their benefits, and then denied it and admitted it in the same Freedom of Information response.
It has arbitrarily sanctioned vast – and rapidly increasing – numbers of claimants, and looks set to impose the maximum penalties of up to 3 years on at least 100,000 people (and more likely 300,000 or more).
Thanks to a tip-off from a reader, I’ve uncovered another in a seemingly endless line of reckless and unreasonable DWP behaviour – not to mention quite possibly illegal, as it must surely breach the Data Protection Act.
The matter centres around the DWP’s ‘Universal Jobmatch‘ (UJM) platform – a system that contains jobs for which jobseekers must demonstrate that they have applied. The use of this platform is routinely ‘mandated’ for claimants – in other words, made compulsory so that non-compliance will lead to ‘sanction’, the immediate cessation of benefits for a minimum of 4 weeks.
UJM has a serious security flaw. Even if a user logs out of the system, the ‘cookies’ it stores are retained unless specifically deleted. If they are not deleted, the next person accessing the system can be logged on as the previous individual – and will have access to all the previous person’s personal information.
Because of new requirements placed on jobseekers, this information does not only include the previous jobseeker’s job-search history, but all of their personal information including a full CV – which jobseekers are now ‘mandated’ to upload.
This problem came to light after a mother and son, who are both JSA claimants and who have asked not to be identified, logged onto a public computer in succession. Because they can’t afford to have a computer at home, they used a machine in a public library.
Mum went first, followed by her son – who accessed the platform and was immediately logged on as his mother.
The mother complained to her Jobcentre Plus manager and received the following response (heavily redacted to protect her identity):


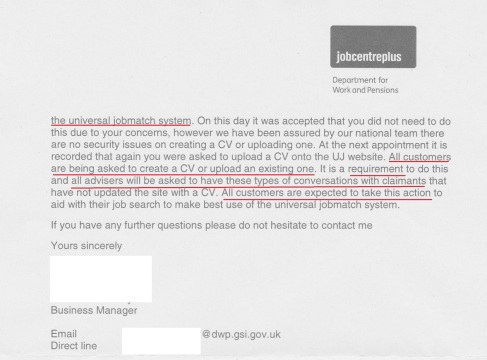
As you can see, the letter claims that there is no such security weakness. But the claimant, fortunately, did not back down. Instead, she complained directly to the UJM helpdesk. The reply she received, while not explicitly acknowledging the problem, did in fact acknowledge it by suggesting the solution:
From: Outgoing-Seeker <Noreply@jobsearch.direct.gov.uk>To: Kathrine Kerr <ktker@aol.com>
Sent: Mon, Mar 25, 2013 10:52 AM
Subject: Reference Number XXXXXXX – I need to report a technical issue CRM:XXXXXXX
Dear XXXXX,
Thank you for contacting Universal Jobmatch.
We have checked our records and we can confirm that we only have your email address on our records. Therefore we suggest that you clear your cache and cookies, please refer to your browsers in line help if you need assistance to clear your cache and cookies.
We hope this answers your query, if you need any further assistance please do not hesitate to contact us.
Universal Jobmatch helpdesk
Kind Regards,Clearing cookies for a specific site is a possible, but time-consuming process if you are using your own computer – and difficult to complete reliably. But on public access terminals in libraries, community centres etc, users are barred from the necessary access to the browser options to be able to delete cookies and private information.
As the above response letter (not email) also discloses, all jobseekers are required to upload their CVs to UJM, so failure to do so can be considered a breach and punished by a sanction of at least 4 weeks.
So we have a situation in which Jobseekers are required to comply with an instruction which might put their detailed personal information at the disposal of complete strangers – and can be punished by the immediate suspension of their vital benefits if they do not, to the severe detriment of the claimant, their family and others.
The DWP’s intrusion does not end with coercion to put personal information at risk of public exposure. I can also reveal that claimants are asked to give the password to their personal email accounts to their JCP advisor.
The official reason for this is so that advisors can check whether acknowledgements have been received for online job applications a jobseeker claims to have made – but possessing someone’s personal email sign-in clearly leaves claimants open to serious abuse, from snooping to potential risks of blackmail or fraud.
I contacted the DWP to ask for their comments on these very serious matters, and received the following reply:
This response is telling in several ways:· Universal Jobmatch is a valuable tool for helping jobseekers find work, and already more than 2 million have registered to use it. The sheer volume of jobs posted on the site means that we expect the majority of claimants who are genuinely looking for work to use it willingly.Where this is not the case and where appropriate we may require some Jobseeker’s Allowance (JSA) claimants to create a profile and public CV.· Claimants are not required to accept cookies. If they don’t want to accept cookies on their own computer, then where possible they can use an Internet Access Device in their Jobcentre (by arrangement with their adviser).· Claimants are not required to allow DWP access to their account – it is entirely up to them – many choose to allow access because it enables their adviser to offer them more personalised advice and support.
- it contradicts the clear written statement by the JCP manager that jobseekers are required to upload a CV. Whatever the DWP press office’s claims, it is evident that ‘on the ground’, the reality is that it is compulsory
- it tries to state that claimants are not obliged to accept ‘cookies’ to use UJM – but the only way to avoid this is to attend the Jobcentre Plus in person.
- it acknowledges that claimants are at least asked to hand over their private email log-ons to their advisors. Even if it is voluntary, it still involves the risk of snooping, blackmail and fraud, as well being deeply problematic in ethical terms – but in view of the contradiction with the ‘ground-level’ reality on uploading CVs, it is completely conceivable that my source’s claims are true: that claimants are being pressured into handing over their private account details.
And whatever the practicalities, forcing claimants to use a system that is known to contain a risk of revealing sensitive personal information – not to mention pressuring them to reveal their sign-in details – must surely be a breach of the Data Protection Act in all kinds of ways, and is therefore illegal.
Once again, we see the DWP acting in a rogue, reckless and bullying way to infringe the rights and dignity of unemployed people – and don’t forget, there are about 500,000 jobs for over 2.5 million unemployed, so this is emphatically not a lifestyle choice. This department – following the example of its Secretary of State – treats vulnerable people with utter contempt and disregard for their rights and wellbeing.
I will be sending this information to the Work and Pensions Committee with a request for its urgent attention on the matter. I ask and urge you to do the same, so that Iain (Duncan) Smith is finally held to account. The email address is workpencom@parliament.uk